
Hackers’ Guide to Aircraft Maintenance

The step change is happening in the air transport industry in regards to data communications, Internet technologies being introduced and increased use of software and COTS-based system, which is creating massive opportunities for those new to the industry. Unfortunately, some of these opportunities are for those with less-than-savory goals.
This article is written from thier point of view — the hackers. The bots (i.e., automated software tools used to access other computer systems). The black hats (i.e., hacker who “violates computer security for little reason beyond maliciousness or for personal gain”). They know who they are. The FBI might know as well …
Why write an article from the point of view of such people? Quite frankly, why not? If the aviation industry does not get more serious about protecting itself as it embarks on the wide-spread adoption of Internet-based technologies which will literally power new-generation aircraft, air traffic management systems, and aircraft support solutions, well, we will be on the losing side of this battle. This is why I am providing you with a quick overview of how hackers could attack an aircraft when it is at its most vulnerable — namely, when it is under the care of a maintenance department. That is when there are no pilots in the cockpit checking systems, software and data are being loaded by support staff, and if the aircraft is in for a check or a repair, it is possibly off in some maintenance hangar somewhere.
Formula for disaster = ((XX new aircraft types entering the market) * (several new ATM systems in North America, Europe and elsewhere being launched) * (YY,YYY’ of retrofitted legacy aircraft with new avionics)) / ZZ,ZZZs of aircraft support personnel who have minimal IT training (at best)
For a hacker, this is quite simply a dream come true. An entire industry where much of the operational side of the business has minimal information technology (IT) skills outside of using some basic applications that management forces them to use. This is coupled with many perpetually cash-starved organizations which go into bankruptcy on a semi-regular basis, so they cannot afford to attract a large amount of tech-savvy personnel, or quite possibly, spend enough to enact proper cybersecurity protection. Heck, the biggest problem may be similar to the one that the lions of the Serengeti have during the peak migration season: which target do I go after first? Truly, an embarrassment of riches to choose from!
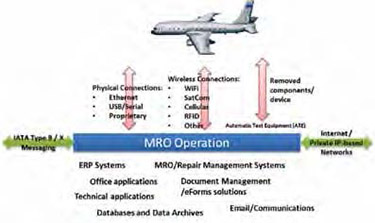
With the increased dependence upon such vulnerable technologies such as GPS, Ethernet-based systems within an aircraft, USB flash drive use, global distribution of safety-related data (manuals, updates, performance and status data) and eCommerce trade of $B’s in spare aircraft parts (some with faked or tampered documentation) via the Internet, wireless connectivity to aircraft, and a number of other product areas, hackers have at their disposal a number of choices by which launch attacks (as shown in the diagram below).
This allows teams of specialist hackers to gather and either attack a fleet or a single type of aircraft or avionics, or attack the back office operations of an operator or MRO operation. We will concentrate our efforts in this article on the support side of aircraft.
Physical Security: Still Needed in a Virtual World
This is not a reference to armed guards (but, it could be) standing around a barbed wire fence around each work station. One of easiest ways for someone to gain access without leaving an electronic footprint (as most network access is logged or tracked in some way) is to physically access a facility and use a known port (USB, Ethernet, serial, modem, etc.) by which to either access and gather data, or download an application which either does so on your behalf, or simply creates chaos in some way. There have been reports of airlines using infected USB drives to load software onto an aircraft or an EFB, one of which was involved in a serious issue. Such actions are made possible when non-IT savvy personnel do not follow procedures to virus scan such USB flash drives or data downloaded off of the Internet. Note to support personnel: always virus scan any downloaded data.
The infamous Stuxnet worm (a type of malware) which shut down Iranian nuclear reactors was apparently introduced via an inside person who was able load the virus via a USB drive into the facility. Stuxnet was designed to traverse networks and computers indiscriminately until it found a specific set of applications which were based upon a particular set of Siemens industrial software and equipment (referred to as supervisory control and data acquisition or SCADA systems that are configured to control and monitor specific industrial processes). Stuxnet infects the target by subverting a specific Siemens-provided software application that is used to reprogram these devices and caused them to operate the equipment it controlled past its design parameters and caused massive failures. Not protecting access to aircraft and supporting systems in your facilities is simply inviting similar problems.
Many aircraft systems use a similar type of design philosophy as some of the newer SCADA systems to control and monitor specific avionics and other aircraft systems, in that commercial real-time operating systems (RTOS) which aerospace companies use to help develop embedded applications which are eventually installed upon aircraft or aircraft-interfacing support systems. There is nothing wrong with using such RTOS or other proprietary approaches, but if the systems which have applications developed for use with these COTS solutions are not designed with some level of cyber protection, then issues such as Stuxnet may infect an aircraft. We have seen other examples of hacking into such previously-closed systems, and now that aircraft are being attached to Internet-protocol networks, expect that issues will arise. While legacy aircraft designed in a previous generation use much less data communications, retrofitted avionics may introduce risks which were never mitigated previously. This creates opportunities for the hackers of the world. Before retrofitting in any avionics, operators and support personnel need to perform comprehensive cyber testing of how an aircraft will react under a cyber attack.
Since OEMs are not in the business of sharing how their systems are designed publicly for good reason, there are steps which would make hackers’ lives easier:
1. No IT training for maintenance staff. Many organizations do not provide much or any training on new or emerging data, communications or computer access technologies to the staff entrusted with supporting aircraft. The less savvy your staff is, the better (for hackers, that is). Note to aircraft support entity: It is recommended that you not only train personnel on the latest avionics interfaces and their behavior (types of data used, how often, how it is secured, etc.), but also in computer security, since most or all modern avionics will either access updated data via some type of port or antenna. Your staff better be able to understand the difference in using a WiFi 802.11b link with WEP encryption, as compared to using 802.11h with WPA2. (If this sentence is Greek to you, check the Wikipedia topic ‘Wi-Fi protected access’).
2. Wireless access points are not usually as secure as they could be. Newer aircraft which have designed-in wireless (WiFi, SatCom, cellular, etc.) capabilities may not secure them properly (assuming that an operator will do so instead), but probably do not always shut them down when they are not needed. (I am not talking about when pilots are playing a game while flying over Minneapolis). This ‘gateway to mayhem’ could easily be closed by simply shutting down such capabilities when they are not necessary to have on for some specific reason. In fact, since there are typically less operational personnel (pilots specifically) monitoring an aircraft while it is being serviced, this is a great time to attack. This was demonstrated via a test (thank God it was only a test) by a cyber-researcher named Craig Wright in Australia who was able to access and modify the control system data on a B747 and its engines via wireless link (which was intended to be used for a video system). While Boeing and the regulators may have closed this open access by now, simply finding the existence of such a vulnerability is disconcerting. Note to aircraft support entity: shutdown unneeded wireless access capabilities when they are not needed as part of your operational processes — or else someone can sit outside of your building and cause havoc without having to deal with stealing or creating ID badges or picking locks.
3. Most companies do not demand additional information or training from OEMs. If you are retrofitting a new avionics system which has greatly increased communications capabilities or generates multitudes of performance data which is off-loaded, most aircraft support departments may not be fully aware of how such data is shared or protected. Ignorance is bliss (to a hacker, that is). Maintenance manuals and bulletins are nice, but in the current globally-connected world we live in, they may not be enough for someone to understand how to enact proper cyber defenses for a facility which supports such aircraft and avionics with such communications capabilities. It is child’s play to find out which operators are procuring which avionics, ERP/MRO systems, and even what types of network gear may have been installed at their facilities. Note to aircraft support entity: demand that OEMs provide you with more information on exactly how data is communicated to and from their systems, and how the OEM designed in cybersecurity controls. Ask them for recommendations on to protect data going to and from their devices (differing types of access methods have differing needs). Do not depend upon the component maintenance manual (CMM) or some other manual only, and ensure that the OEM(s) have provided you guidance on to mitigate risk from a cyber perspective. Mandate that they help you secure yourself when dealing with their products.
There are a number of other steps to take here (e.g., log access to devices via digital credentials, so no one can simply borrow someone else credentials that easily — refer back to my previous article in this magazine on this topic), but these main issues need to be addressed as part of your internal processes from a non-virtual perspective.
Living in a Virtual World
Now that you know some of the steps to take to protect yourself (train your staff, shutdown wireless access when not needed, get more info from avionics and aircraft OEMs), let’s look at how a hacker can penetrate your virtual defenses.
The weakest link is arguably a tie between differing technologies:
1. As discussed in the previous section, wireless access (especially WiFi, which is less secure than most of wireless technologies) is usually the weak link in any organization.
2. Just as weak is the simple old login/password scheme (view the text box on the right). Organizations which have not moved to strong passwords (which is quite simply requiring the use of a password which has eight characters or more, contains an upper-lower case mix and a numeral or a special character — not that this is not a technology solution, but just a process solution), are at risk. Note to aircraft support entity: If you are not already implementing some form of strong passwords, you are simply taking all of the fun out of the situation. Be a sport and make it more challenging for the hackers.
Hackers are more than happy to take the low-hanging fruit you provide.
Another set of issues revolves around the industry using ERP or maintenance software from a handful of vendors. With most large software applications supporting Internet or network access to data, trading partners or other business partners, along with cloud-computing functions (for remote data backup, data updates, scheduling with partners, eCommerce functions, etc.) , cyber risks to such critical data is greater than ever. In fact, with the increase in collaboration amongst companies (so that customers will always have access to the latest data, production schedules, inventory information, etc.), hackers have never had it so well. More targets, more data to choose from.
IT departments are typically tasked with protecting such applications, databases and private industry networks (IATA Type B and X). But, once again, the IT departments are not the weakest link here. It is the non-IT staffs who use these applications and who may introduce problems inadvertently by downloading unapproved software, which may be malware designed to specifically target specific applications. Malware can often ‘phone home’ once it acquires targeted data. The best cyber defenses can be undone by the lack of training or process controls. Organizations which get by without investing in their people will eventually pay for price for not doing so.
One of the best ways to infiltrate a target is via ‘social engineering’ (refer to the sidebar on top). Despite all of the attempts by Nigerian princes wishing to give you a cut of their fortunes if you merely provide your bank account, this form of deception is still incredibly pervasive. Due to platforms such as Facebook, in which a myriad of applications acquire your personal data, it has become almost accepted to be contacted for your personal information.
For a cyber attacker to bring an airline or MRO to its knees, gaining access to a records/document management system and compromising the integrity of a small amount of such data is all it would take. You can only imagine how long it would take to restore back such a system to a ‘trusted’ state (in some cases merely hours, in other cases, days or even weeks). Note to aircraft support entity: the best way to defend against this is quite simple — train your staff on such issues, and enforce strong passwords which are changed frequently, implement strong logging mechanisms to track who did what and when, and backup off-site frequently. Run scenarios in which you test your ability to restore an entire working IT system back to a working, trusted state.
Software data loading onto avionics, components, and devices such as EFBs is another issue. While some of this may be performed in a (semi) secured maintenance facility with a stringent network controlled by a savvy IT department, it is not always so. Especially with many of the newer iPad-based EFBs which pilots are allowed to remove from an aircraft and bring them to hotel room, where unsecured WiFi access is the norm (not to mention using it at a Starbucks near an airport gate). While none of this is guaranteed to introduce cyber issues to the EFB (or the aircraft that they interface with), it creates more opportunities for cyber attacks. Once again, thank you.
What Hackers Do Not Want You TO Do
I think I have provided plenty of scenarios of how cyber thieves could infiltrate the aircraft maintenance environment, so allow me to swing back and provide ideas on how to counter some of this.
To avoid a majority of issues identified here (and this article was not intended to be a comprehensive list by any means … you need to do a lot more reading other than this short synopsis), do the following:
1. Use strong passwords, and change them regularly. Do this on all of your systems: MRO/ERP and other applications, EFBs, test equipment, wireless access points, and most of all, on your work PCs.
2. If you need to use wireless, understand the limitations of the standard you are using (hint: WEP has been broken, and WPA2 is what you want to use as a minimum … Google those terms for more on this).
3. Turn off wireless access when it is not needed. Make this a habit.
4. Have cyber professionals do testing on your facility, networks and applications whenever major changes have occurred. Implement recommendations provided by these people. Re-visit your procedures on a regular basis. Airlines, MROs and other aviation entities need to conduct “cyber risk assessments” to determine their vulnerabilities, risk mitigation/countermeasures in their operations and/or aircraft. This is a new emerging type of proactive set of actions, and you will be hearing much more about this in the coming year or two. Get ahead of the curve and look into this ASAP. Do not wait for your IT department to get around to this. Hint: audit logs are a key tool for determining how systems are compromised and how to enact better controls.
5. Training — you can never do enough of it. Train your non-IT support personnel on key cyber topics and technology issues (wireless and network security concepts). They do not need to be experts, but they need to be aware of key elements.
6. Appoint at least one key ‘point person’ to monitor and be aware of cyber issues as they occur in the outside world, as they relate to your operation. If you run a SAP ERP and MRO set of applications, and support aircraft with Honeywell avionics primarily, then have your IT staff setup monitoring of any news which related these (Google Alerts is a free services which you can easily setup and use), and have the point person check this daily. The more aware you are of issues affecting others (globally), the better you can mitigate potential risks to your aircraft or operations. Be vigilant and involve your non-IT staff.
7. Either participate or monitor key industry standards activities in these areas. This is a rather new topic for aviation, so standards and common criteria are changing rather quickly. Stay on top of this. You may not need to invest time in being part of these activities, but you should be aware of them and what is being discussed (and why …). Two key standards every organization should thumb through are ARINC 811 and NIST 800-30, among various others.
8. Another item of interest is how information sharing and analysis centers (ISACs – go to “isaccouncil.org” for more info) will affect the aerospace/aviation industry, since we are one of the last sets of identified industry sectors not to have one (these exist for banking/finance, utilities, shipping/cargo/trucking, electronics, and various other sectors). What this provides is a means by which affected companies can anonymously report cyber incidents to help others, and also receive warnings (and guidance on how to mitigate) of such incidents. There are many other services these provide, but for purposes of this article, this should be enough for you to contact your FAA or DHS contacts to inquire about this.
Finally…
Please keep in mind that none of this should be considered an exhaustive or complete list of cyber issues. Hopefully this article scares you enough to ask questions within your organization to address some of the issues identified here, as well as others that your team may come up with internally. While the cyber-related risks are increasing to aircraft
and related systems, the greater capabilities that Internet protocol-based networks, wireless in all of its forms, and increased data communications provide to aviation far outweigh the perils.
We are in the midst of a technology-driven upheaval in how aviation will manage itself, which will bring some near-term problems, along with longer-term benefits. Now is the time for existing organizations to prepare themselves to handle the challenge of protecting aircraft in the cyber age, and for new entities to arise which will bring novel solutions to overcome the test presented by hackers and those who would bring chaos to our industry. This is also the time for motivated individuals to seize the day within their organizations and move their operations forward.
Carpe diem!

